How to Secure Your Website on Shared Hosting?
Shared hosting is more affordable than other options; however, this hosting plan can be more prone to data breaches.

Shared hosting in the UK or any other environment seems to be the cheapest alternative. This kind of hosting is generally fast and scalable although security can be a problem. With many users sharing a single server, the risk of data breach is higher than other types of hosting. Web hosts like Jolt.co.uk practice strict security measures. However, serious threats remain which call for more caution.
Ideally, each user must be isolated from other server users to prevent unauthorised access or modification of files. They must have individual remote database access and must not be allowed to change records or table permissions of other websites. Shared servers are updated and monitored regularly to resolve security problems. Here are several valuable pointers that we wish to share with website owners regarding shared hosting.
Clean Website and Passwords
Remove any idle email account and File Transfer Protocol (FTP) accounts as well as other unused apps and files from the server. Additional files make backups that take longer. Fewer files mean better chances of locating something which is not in the proper location. Get rid of redundant scripts. Hackers usually manipulate obsolete scripts site owners may have omitted.
Use different strong passwords for FTP accounts if you use Secure Shell or SSH Protocol, MySQL databases, and Content Management Systems. Cyber thieves who crack the password can spoil your website. Change the codes frequently using a combination of letters, symbols, and numbers.
Avoid the use of common terms, names of family members, or birthdays because these can be deciphered easily. For CMS such as Joomla and Drupal as well as Learning Management Systems like Moodle, use a password for admin login as additional level of protection. This precaution prevents hackers from identifying apps running on the server.
Backups and File Permissions
Web hosts usually perform regular backups. However, it is not enough to rely solely on their services to safeguard information in your site. Hosting firms’ backups serve as duplicates, but it is recommended that you set up your exclusive backup off-site. Choose between basic file managers in downloading files to your PC along with databases required to make the site functional.
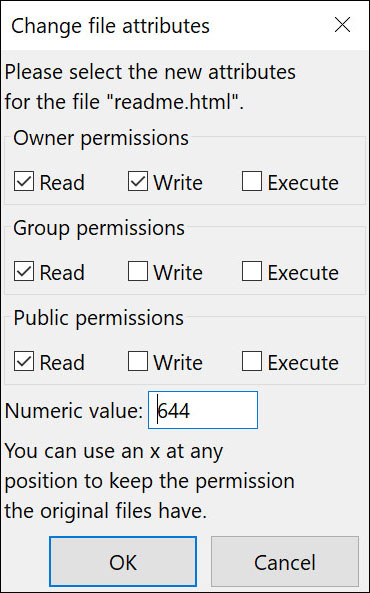
Do not give the public access to certain private locations on the website. Set permissions for read-only files properly. For example, using 7-7-7 will just encourage Internet crooks in gaining access to your site and deleting or modifying files. File permission indicates who can access, read, write, and revise files. WordPress needs access to write-to-files in the content directory for allowing particular functions.
CMS needs specific permissions to function correctly. Consider your current permissions through a screenshot before making any changes. If the site suddenly stops functioning, you may have changed file permissions incorrectly. Check the documentation for apps running on your site.
App Updates
It is important to subscribe to security releases and updates related to your application regardless of software you use on the website. Once a new CMS update appears, do not wait for auto-install script to update with the most recent upgrade. Many hosting firms and data centres use Softaculous installer for better results. It has 447 scripts together with 1,115 Personal Home Page (PHP) classes.
At the same time, know how to perform upgrades and see to it that everything is updated. Updates secure websites from security risks. These also improve users’ capacity to keep away unauthorised users from taking advantage of obsolete applications or programs.
Monitoring Scripts and Forums

Some website owners share their sites with friends. However, it gives hackers the opportunity to send out unwanted emails which can turn out as malware. Monitor and update your scripts as protection against malicious software or unsolicited mails. Keep emails away from the website’s public area. Opt for password-protected logins to ensure only authorised users gain access to defenceless areas of your site.
Make sure to disable the option for other users to insert codes if you have website forums. Choose between Hypertext Markup Language (HTML) and Java Applets for public forum posts. This Applet is a special Java program that browser-enabled Java technology can download and run from the worldwide web. It is usually embedded in web pages and operates within the context of browsers.
Disallow users with malicious codes from registering on your site. In the case of public forums, employ extra security measures that will prevent other people from injecting codes into your portals.
Java Apps
Java refers to the class-based computer programming language. The program provides flexibility. Web developers utilise Java to build custom applications. Java also supplies information regarding used PCs that can be accessed by expert hackers. As a preventive step, enable access to special features only to registered users in your site. It does not totally eliminate the likelihood of getting codes but offers more protection for shared servers.
Computer Protection

FTP programs may be compromised by using unprotected computers. Viruses and malware take advantage of these programs for accessing files. Install dependable antivirus software on your computer with the capability to monitor intruders. Disconnect the machine if you are not using the Internet so unscrupulous individuals cannot access your system. Refrain from storing passwords and confidential information on online computers. When they obtain passwords illegally, it will be easy for them to read your bank information and private files.
Installation of Content Management Systems

The CMS is an app or group of related programs utilised in creating and managing digital content. These are used mainly for Enterprise Content Management as well as Web Content Management. Common CMS include WordPress, Joomla, and Drupal because of their user-friendly interfaces.
Here is the catch. Online thieves who detect your password can exploit weaknesses making it easier to breach the website. Whenever possible, conceal plugins so browsers cannot easily identify the CMS. Or, install extensions that remove said information from website files.
Safe Mode
Turn on Safe Mode, the diagnostic mode of the computer’s OS. The troubleshooting option restricts Windows operations to the fundamental functions. The PHP script enables users to retrieve information on the shared hosting environment. Be sure the PHP settings are accurate to stop illegal users from executing scripts. In case you are not familiar with the process, check out your host’s technical support to address the issue. Bear in mind that without this Safe Mode, any user has the chance to run the script that contains all your passwords, directory, files, and sensitive site information.
Databases
The database is the structured collection of data in a computer and can be recovered in various ways. The first preventative measure is to avoid keeping private information in any website file. Instead, use a database for safekeeping sensitive data. Databases are used automatically for almost all applications. Nevertheless, certain apps offer options in using the server’s hard drive or the database in preserving session information. Choose the database option if possible for acquiring extra security layers on your site.
Configure the .htaccess
Linux websites provide an alternative for users to set up privacy references in .htaccess file. This open-source OS is based on UNIX, a popular operating system. You can insert multiple code snippets for more security. Prevent any unlawful access to your .htaccess file by setting the permissions to 644 thereby preventing visitors from opening specific files.
Supplementary measures consist of the following:
- Limiting access to particular files
- Averting browsing of the directory without your permission
- Changing the default index page to protect the site
- Hide script extensions
- Secure directories to the LAN or Local Area Network and specific IP address so only you can open such files
Web Hosting Provider

Finally, one of the effective methods in protecting your website information is to look for a competent web host capable of offering solid security. You need to review carefully published reviews about hosting companies in the UK. The provider must have the expertise and staff to conduct monitoring and prevent the infringement. This will deter any hacker to see your files. The well-equipped host utilises scanners and apps providing premium protection.
Final Advice
One downside of shared hosting is the unprotected environment which permits hackers to potentially steal information from websites. The upside is users have a lot of choices when it comes to security. You may upgrade to any of the following:
- Dedicated
- Semi-dedicated
- Virtual Private Server (VPS)
Do not store credit card details or personal data unless you have installed a Security Sockets Layer (SSL) Certificate. If you do not feel capable of making revisions or implementing anything on your site, find an IT expert or seek the assistance of the web hosting company for tasks associated with server protection. Otherwise, you must take responsibility for anything that happens to your website.
About Jolt UK Hosting
Jolt Hosting UK is one of the more reliable web hosting providers based in the United Kingdom and all over Europe. Go over its website at http://www.jolt.co.uk/ or send any queries to feedback@jolt.co.uk.
