How to Secure Your Website with cPanel
Learn how to secure your website with the help of cPanel. Doing so will safeguard your website from attacks.

No one knows the value of security for websites more than experts like web hosts in the United Kingdom. Server security is vital in safeguarding websites and other valuable data from hackers, malicious hardware, and virus.
The cPanel Control
The efficient cPanel is one of the most widely-used and recommended by web hosts. It is trusted by web developers in different countries to help them manage websites and hosting accounts. The cPanel Company says one hosting account is built online every 14.5 seconds. However, its popularity has a big downside, which is being a target for breaches. Threats make security a crucial factor.
Where do you start in securing the cPanel platform? It appears complicated, but the simple configuration is a boon for users. Here is a guide that can assist you in securing websites using cPanel.
Updated Version
Get the newest version. Otherwise, the risks increase.
Update cPanel: WHM > cPanel > Upgrade to Latest Version.
By using the newest version, you can access all bug remedies and security enhancements. Creators of cPanel has simplified everything by installing the Upgrade to Latest Version option on the homepage. Users only need to facilitate automatic daily update of the server. Go to Update Preferences under the Server Configuration.
Passwords
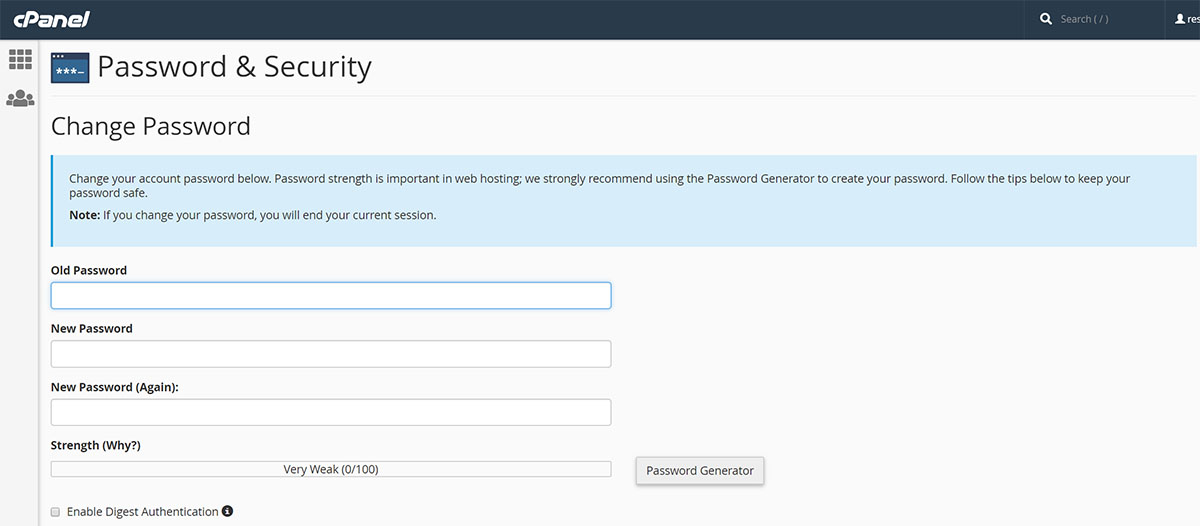
Use safe passwords. Change them if needed. Keep in mind that a strong password is not easy to hack. You may use the cPanel’s password generator tool for suggestions. By defining your secret codes, you avoid the default configuration that utilises the same user ID as well as password for user and File Transfer Protocol (FTP) accounts. To prevent intrusion, enable the Security Sockets Layer (SSL) for access to the control panel through Tweak Settings found in Server Configuration. To thwart the possible hacking of user-level accounts, configure the password strength so users are compelled to choose hard-to-crack codes.
There is an option to protect selected files (for sharing with certain users) with passwords.
- Go to Files. Click Directory Privacy.
- Choose Web Root. Click Go.
- Proceed to the folder that you want to secure with the password. Click the name.
- Check the Password Protect this Directory. Enter a name. It will appear in the login pop up once you access files.
- Press Save. The folder has just been secured.
- Create a username and password for accessing the folder. Accomplish all the required fields in Create User section. Press Save again.
Now, navigate to any file in said folder. Input credentials after you are prompted allowing access to your file.
Firewall, Anti-Virus, & Anti-Rootkit
The ConfigServer Security and Firewall (CSF) is a popular app for the cPanel server. It provides suggestions for increasing security. You may use the Clam Anti-Virus, a free open-source and cross platform. This software toolkit can detect different kinds of malware and viruses. It functions as server-side email virus scanner.
Hotlink Protection
Website images must be stored in a specific place of the server. You must prevent unauthorised users from locating the URL to an image and embedding it to another website. It is like stealing your bandwidth resources or Hotlinking which exists in files and images. cPanel offers a solution known as Hotlink Protection that safeguards files and preventing them from being inserted in third-party sites.
- Navigate to the Security Section.
- Click Hotlink Protection to make sure it is enabled.
- Add domain names authorized to access your files by including them in URLs to Allow Access. cPanel will include said domains automatically.
- Enter the list of file types you want to secure in Block Direct Access for the following extensions. Enter the list to stop hotlinking of images, media formats, and other file formats.
- Check Allow Direct Requests. If not, it may affect the functionality of your website.
Credentials Outside the Web Root
It is necessary to keep credentials in your server. Store these records outside the public website folder for security reasons. Servers that use cPanel generally stockpile public website files in the folder called Public_HTML. Backend processors like the PHP can reference credentials whenever required.
- Proceed to Files Section.
- Click File Manager.
- Choose Home Directory. Click Go.
- Create new folder in the home directory. This is outside Public_HTML.
- Store the credentials in the new folder.
To access the records from your app, set up a relative reference to these credentials that can be accessed through a separate folder with the same name.
Safe SSH
The SSH allows remote access to servers that run cPanel. There is a basic command line interface which may be the best method of fixing, updating, or making reconfigurations. The default port number 22 is common. To prevent breaches, redefine this port number that third parties cannot guess. Choose a difficult set of numbers. Select a port that is not currently used. Change the system configuration if needed. Use version 2 instead of version 1 of the SSH. The SSH changes are implemented by editing SSH daemon config file.
Brute Force Protection
Set the value of this limitation to block repeated attempts in accessing your server from the IP address. That IP address will be logged in the database of your cPanel. cPanel can accept another login attempt from that IP address after a specified duration. In activating the functionality, proceed to CP Hulk Brute-Force Protection found at the Security Center. Click Enable. The IP Deny Manager allows you to identify an IP address, domain name, or several addresses that should be prevented from accessing cPanel-managed websites.
Unspecified FTP
Disable unknown FTP. Or else, hackers can upload content and access your account. You achieve security by immobilising the anonymous File Transfer Protocol as well as indicating the SSL for access. Perform this function in FTP Server Configuration. Set the Allow Anonymous Logins to NO.
Securing PHP and Apache
cPanel has a utility named Easy Apache to build and compile new Apache server versions as well as PHP scripts quickly. This approach helps the user restrict malicious scripts within the home directory and prevent them from opening any files. Navigate to PHP open_basedir Tweak found at the Security Center and check. Save the Enable php open_basedir Protection.
Security Check on Hosted Websites
The Site Security Check cPanel function verifies threats to domain names linked to hosted websites. Users have the tendency to focus on containing user access to the cPanel or sites this panel manages. They forget to examine the website’s nature. It will reflect negatively on the reputation of your company and affect profitability if domain names are cited as potential threats by tools like Google’s Safe Browsing.
Security Checklist
Aside from password strength concerns and control of open_basedir PHP scripts, other options for improving security are deactivation of compiler access for unnamed users, restricting use of su command to become root user, and defining the Shell Fork Bomb Protection in preventing users from having unlimited access to server resources. cPanel contains more options for security enhancement. Read all instructions carefully for a more protected and high-performance server.
Modify Settings Checklist
The Tweak Settings Section at Server Configuration provides multiple security options. These alternatives include the following:
- Use of Cookie IP validation to limit the likelihood of hackers capturing cPanel session cookies and attempting to access cPanel
- Use of security tokens to access cPanel, and the “Bounce” option to discard emails that cannot be routed and protect the server against email attacks.
Create Limited Functionality for Database Users
For websites to access databases, supply the credentials of database users. Which credentials must be utilised? If the web host provides credentials for root database users, do not use this information in your application’s code. The root used provides complete access to your database. This move can cause security risks. cPanel offers an option for allowing the users limited access to specific functions.
- Proceed to the Databases section. For MySQL databases, click the MySQL Databases. For PostgreSQL databases, click the PostgreSQL Databases.
- Accomplish the required fields in the Add New User section. Remember your username and password.
- Relate the user you created with your application’s database. Choose your application’s database and the user you just created in the Add User to Database section. Click Add.
- Choose only the database privileges that your user needs. Limit functionality to INSERT, SELECT, UPDATE, and DELETE. This is normally appropriate for an application.
- Add the newly-created user credentials to the code. Keep these credentials in a secure location.
File Indexing
Finally, disable your file indexing. This index is a public list of all files in a folder on the server which is a security threat. Listing files will encourage hackers.
- Proceed to the Preferences Section. Click Indexes.
- Choose Web Root. Click Go.
- Click the Public HTML text link. Do not click the folder icon.
- Choose Indexing and Save.
Now that you have just gone through this guide, it will be easier to understand the fundamentals of cPanel Security.
